Fast And Efficient Cloud Scalability: How PrestaBR E-commerce Development Agency Handles Traffic Spikes Using Layershift Jelastic Hosting – Case Study
PrestaBR is an e-commerce development agency, specialised in PrestaShop Platform since 2011. They are using Jelastic to host and manage medium and large size e-commerce stores they develop for their clients.
Jelastic is a cloud platform as a service, built to deliver instant server scalability for resource-intensive websites and applications.
Experiencing performance issues during traffic spikes and increased costs for hosting resource intensive e-commerce websites, Thiago Ferreira – Projects Director, decided to look for a better solution to host his client’s websites.

“We were looking for scalable hosting to control simultaneous access spikes” – Thiago Ferreira, PrestaBR
PrestaBR needed a reliable cloud solution that would help them scale multiple websites with high traffic needs. There are several providers on the market and Thiago tested and compared some of the most popular ones such as AWS, Google Cloud and Microsoft Azure, before deciding to use Jelastic Cloud Platform.
“Jelastic is really amazing; it provides very fast and efficient scalability, both vertical and horizontal while also giving us the ability to manage multiple accounts simultaneously using a very user-friendly interface”
Finding the right Jelastic hosting provider
Jelastic is a powerful cloud platform offered by several hosting providers with infrastructure across the globe. There are several things to consider before choosing which provider is best for you; such as datacenter location, performance, customer support, server management level, price and others according to any specific hosting needs you might have.
After testing more than 20 Jelastic hosting providers, choosing Layershift was an easy decision for Thiago. The server performance and efficient customer support, included backups and additional services differentiated Layershift from other Jelastic providers.
“The quality of network and hardware are exceptional at Layershift. Their support is very efficient, friendly and competent. They offer backups to separate isolated hardware, a full copy every 6 hours, retained for 14 days. Also, they offer complementary services like CDN and Firewall with PCI Compliance. The service they provide is very stable and the prices are also great”
Benefits of using Layershift Jelastic
Using Layershift Jelastic has brought many benefits to PrestaBR, the most impactful being “simplicity and practicality, it gets much easier to solve various day-to-day problems” – says Thiago. He had no problem getting started with Jelastic as the extended documentation and support, plus a user-friendly interface allowed him to get used to working with Jelastic platform really fast.
“I had no problems to start using Jelastic, it was really easy. Consulting the documentation a few times, some small clarifications, I got used to working with it within a week”
Being able to scale your server resources to cope with high traffic demands at any given time, is crucial for any e-commerce business as it will directly reflect on your profits. PrestaBR wanted to offer their customers a hosting solution that is not only performant at scale but also cost-effective.
What about costs?
It is well known that e-commerce websites can be resource intensive and you can’t really predict the required resources in advance. Not to mention paying for extra resources you might or might not need, can easily drain your budget resulting in decreasing your business profitability.
Thanks to the pay as you use pricing model, Jelastic not only was scaling server resources according to traffic demand but also allowed PrestaBR to pay only for the exact amount of resources consumed, resulting in cost reductions for all of their customers.
“About costs, all our customers have been positively impacted and are extremely satisfied. A great example is the store www.westcoast.com.br, the saving is around US$ 6k/month”
PrestaBR has been successfully hosting e-commerce websites with Layershift Jelastic for over two years now. If you are looking for a cloud hosting solution that can easily scale and deliver high performance for your e-commerce store, you should give Jelastic a try:
Test how Jelastic can improve performance for your ecommerce websites with a 14 days trial offered by Layershift.
High-level app development with CUBA.platform on Jelastic PaaS
We’re living in a fast-paced world where everything needs to be quick, easy and cost effective in order to be competitive. With the help of frameworks, modern development has become a lot simpler, even for complex applications.
CUBA.Platform is a high level open source Java web framework most suitable for developing enterprise applications with rich web interfaces, complex data models, enhanced security requirements and support for a multitude of business processes.
Being a high level framework, it abstracts developers from underlying technologies — such as Vaadin, Spring or EclipseLink — so they can focus on the business tasks, empowered by a rich set of features and development tools, and without restrictions to low level code.
All you need to develop apps in CUBA is Java SE, XML and JPQL. In addition to a more uniform and easy to maintain code, it also reduces requirements to your dev team as you don’t need any Java EE gurus.
Conquering the world together: Layershift Jelastic PaaS expands to Asia
Asia, here we come !
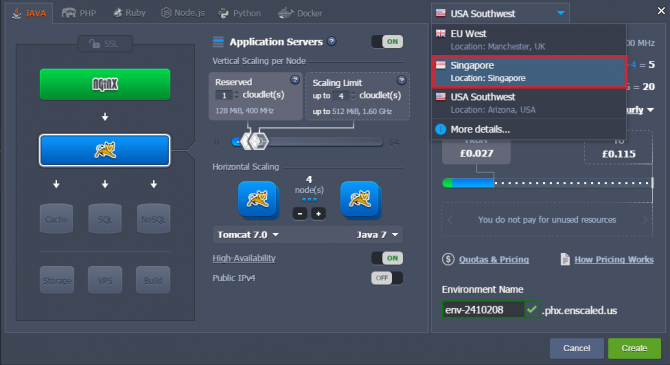
Exciting things happen when Layershift and Jelastic combine forces. We listened to your needs and didn’t rest until we made it happen. We are very pleased to announce that starting today we are bringing the world closer to you, by launching Jelastic PaaS in Singapore, Asia.
Layershift’s partnership with Jelastic started four years ago by offering the unique Jelastic multi language PaaS, on UK SSD servers. In 2015 we expanded our services and started offering it in US too. One year later, here we are, proudly announcing the availability of Jelastic platform in another new location (read official release note).
This makes Layershift the first and only hosting provider to offer the innovative Jelastic technology in Singapore, and as is the Layershift way we’re doing it on top of powerful SSD servers to give you the very best performance.
“We are raising the bar of Jelastic Cloud in Asia; we are the only ones offering pure SSD in the continent, and I’m delighted to be able to bring our strong service and performance levels to South East Asia.”
– Damien Ransome, Layershift’s Service Director
And we are not stopping here, we promise. We are continuously working on exceeding your expectations so when you need reliability, power, high availability, topped up with outstanding support, you’ll know you can count on us to deliver right at your fingertips.
Increased performance around the world
Jelastic is a scalable platform as a service, built on containers, designed to host Java, PHP, Python, Ruby and Node.js applications on Public or Private Cloud.
By choosing Layershift as your hosting provider you can easily deploy your application throughout environments across three continents, in three different regions, all managed on one platform.
When creating an environment, you can choose your prefered location with one click and your app or project will be hosted on the server of your choice almost instantly. You no longer have to buy multiple servers from multiple vendors across the world, we just made things easier for you.
Enabling a third server location in our Jelastic platform, comes with great benefits:
- Simpler management of your projects from one dashboard. You only need one account to host multiple projects in the same time, in different location, across 3 continents.
- Reaching your targeting market faster, without any CDN needed, will minimize your cost significantly without affecting performance.
- Same level of security and power for your project provided by highly secured datacenters infrastructure and SSD servers, in all three locations.
- Award winning customer support and server management, without any extra charges, no matter the location of the server you choose.
- All of our platform’s great features are available in all locations, no difference whatsoever.
Looking forward to welcoming you !
Why wait any longer? Jelastic PaaS 14 days free trial is available so you can convince yourself about the power of the platform designed by Jelastic team, as well as of the outstanding 24×7 customer support and server management provided by Layershift.
You’ve got nothing to lose, we’ll help you get up and running in the Cloud in no time and we’ll make sure you have everything you need along the way. Our award-winning support is included free.
We’re sure you won’t be disappointed, but don’t take our word for it, check our rating and see what our customers say about our services.
Then go ahead and give it a try for yourself!
Phone support? Think again!

The power and clarity of the written word is undisputed. There’s a popular saying “if it’s not written down it doesn’t exist”. It’s widely used across many different aspects of business, and for very good reason; explaining complex issues in written form forces a certain clarity that cannot be delivered orally.
Imagine that you need help with a technical problem. Explaining the steps in writing is the perfect way to get the information across clearly and unambiguously. When mistakes and misunderstandings cause delays and cost money, this is the time when you definitely need to be as clear and unambiguous as possible. It’s the perfect medium for hosting service technical support.
Providing all support via email / helpdesk tickets has led Layershift’s support to be formally recognised as offering the best in Western Europe for the last 2 years running (2014 and 2015).
It’s clear that our support systems serve our customers’ needs extremely well. Even so, from time to time we get a pre-sales request asking why we don’t offer technical support via phone. We understand the apprehension; if you’re used to struggling through with other hosting companies who often take days to respond, only to provide inadequate assistance even when it finally arrives – the immediacy of phone support appears compelling. Even though waiting on hold wastes your time, and talking to the wall yields no results, it all seems like a good idea at the time… but truth is it’s not. Not at all. Here’s why:
5 reasons why we don’t leave our customers on hold
Why Layershift Support is winning
The results are in, and what an amazing year it was! Great customer support is not just an aspiration at Layershift, it’s our passion – the core strand of our DNA. It completely defines us as a company, as a group of talented individuals, as a team.
For others, providing support for their product or service is an inconvenient cost. An overhead. A headache they have to live with. Most of their time is spent dreaming up ways to reduce the support burden.
The results are plain to see. How many support departments did you deal with during 2015? How many actually gave you a good experience? I’m willing to bet the majority spun you round in circles so many times they made you wish that you’d never even asked! This is what happens when support is not central to a company’s ethos. When support is a burden, support is bad.