Using New Relic on our Jelastic PaaS made easy
In the wake of Black Friday / Cyber Monday, you’re probably not alone if you’re scratching your head wondering how to make sure your January Sale runs a little smoother!
New Relic is one of the most popular tools to monitor application performance and identify troublesome code bottlenecks. Such deep insights are invaluable because they enable you to focus your effort on the parts that need you most.
The immense flexibility of our Jelastic PaaS means it was always easy to install New Relic on a Java based environment, but now we are pleased to offer an easy solution for PHP environments too!
All Layershift Jelastic PaaS customers can now install New Relic on their PHP environments with just a few clicks.
New Relic – A watchdog you want to keep safe
There are many application monitoring services that will keep vigil and inform you if something goes wrong, but unlike most New Relic is not focused on your uptime. It focuses on performance.
Almost uniquely, this tool enables you to drill down through your code, so you know which specific function calls or SQL queries were executing slowly – not just that the overall response to the end user was slower.
Of course this is combined with a lovely sprinkling of RUM (real user monitoring) features and general performance tracking alerts to round out the solution.
Overall we think this makes New Relic a really useful companion for any production server, as it allows you to keep a close eye over your app performance AND know what steps to take if performance starts to degrade. This is crucial when it comes to maintaining user experience during those seasonal traffic peaks.
Improving DevOps Agility through a Hybrid Approach
The DevOps approach means you will be handling more than just a single aspect of the product cycle. However, being stuck with acting as system administrator for your company can be a bad thing.
 Since the practice was conceived back in 2009, the DevOps culture has launched a coup in the world of software development. By combining the development and operational aspects of building software, this approach has significantly improved the product cycle, enhanced the performance of software produced, increased the output of developers and has led to far better results overall than traditional IT development.
Since the practice was conceived back in 2009, the DevOps culture has launched a coup in the world of software development. By combining the development and operational aspects of building software, this approach has significantly improved the product cycle, enhanced the performance of software produced, increased the output of developers and has led to far better results overall than traditional IT development.
By involving developers at every stage of development and deployment, it has become easier to create more stable software with better-integrated components. Developers are now involved in the software development cycle from the beginning to the very end. As a result, operational functions such as customer service and quality assurance are also being handled by developers under this approach.
At the same time, DevOps has led to a greater involvement of users in every phase of software development. This is one of the key aspects that helped improve the quality and efficiency of beta testing over the past few years. And with the improvement in beta testing, the consequent quality of final versions has steadily improved.
MongoDB Replica Set automatic deployment
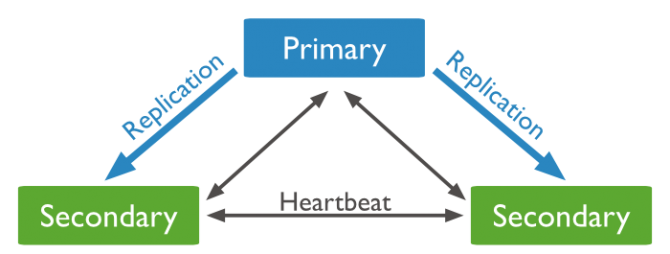
MongoDB supports master-slave replication and a variation on master-slave replication known as replica sets. Replica sets are the recommended replication topology. What is the difference?
Replication vs. Replica Set
MongoDB’s replication is “single-master”, meaning only one node can accept write operations at a time.
In a replica set, on the other hand, if the current “primary” node fails or becomes inaccessible, the other members can autonomously elect one of the other members of the set to be the new “primary”.
Why High Availability Is Important for Your Business
 Today’s businesses are addicted to IT. Every part of the business now needs Internet connectivity to function, and not just for cat videos during breaks; from communication via email, instant messaging, and VoIP, to back office ERP and CRM – not to mention the importance of digital marketing channels and ecommerce.
Today’s businesses are addicted to IT. Every part of the business now needs Internet connectivity to function, and not just for cat videos during breaks; from communication via email, instant messaging, and VoIP, to back office ERP and CRM – not to mention the importance of digital marketing channels and ecommerce.
Applications, and even consumer-facing services, are now shifting to cloud and hybrid models as companies realise that in-house IT, once tasked with running an Exchange server and maintaining desktops, lack the tools and specialist expertise to keep these systems running.
Our heavy dependence on the Internet to get business done exposes a threat with the potential to transform the competitive advantages of this new world of doing business in the cloud into a business killer.
Block malicious traffic with fail2ban
 There are many ways in which you can protect your VPS – from strict password policies, through to aggressive spam filtering, basic firewall configurations and antivirus. However, no matter how fancy and elaborate your security precautions are, there will always be someone ready to launch dictionary attacks and probe for vulnerable scripts on your poor server.
There are many ways in which you can protect your VPS – from strict password policies, through to aggressive spam filtering, basic firewall configurations and antivirus. However, no matter how fancy and elaborate your security precautions are, there will always be someone ready to launch dictionary attacks and probe for vulnerable scripts on your poor server.
Even though we preconfigure strict firewall policies on our fully managed Cloud VPS, there are some services – like the web server itself – that have to remain wide open to the world. Without those gates, there would be no mail flow or web browsing.
Consequently your Cloud VPS can be kept quite busy just fighting off failed FTP/S password probes along with the load of “404 not found” reports in your apache error logs from bots searching for common software exploits. Not to mention the wealth of failed IMAP, SMTP and POP3 connections from spammers and identity thieves trying to compromise your mailbox.
If you weren’t really careful about keeping your website software 100% up to date you have, probably, at some point, received a support ticket from our abuse department notifying you that your VPS has unfortunately become a spam crib due to malware injections or a simple password breach.
A few months ago Parallels (now Odin) introduced new security enhancements to Plesk 12. Such features as WordPress Toolkit, mobile manager application, antispam and antivirus capabilities; the platform is a great choice for any web administrator. One little gem, in terms of security, was the addition of Fail2Ban. Let’s take a look at how it works and how it can save your server from compromise.
